We always want to follow the least privilege security principle when granting permissions. Is role based access control alone sufficient to achieve this?
There are several challenges
- If permission given indefinitely without an expiry, it will cause a risk
- Such users may leave the organization
- Projects may end
- Having higher permission without a need at the moment is also a risk
- Credentials can be compromised at any moment
- You may do mistakes with higher permissions
Privileged Identity Management (PIM) is the solution for this. Microsoft Azure also provides a PIM facility which is an Azure AD premium (P2) feature. This article will provide an overview of Azure PIM features.
Azure PIM allows you to grant users and groups elevated privileges to Azure AD and Azure resources whenever necessary.
We will take a scenario to explain the concept.
Lat's take Contoso, which is a Financial organization which has its workloads in Microsoft Azure. John is a systems engineer who works in the same organization. Time to time the business requires to build new VM workloads and to modify existing VM resources. John should not have permanent contribute access due to prevailing audit and compliance requirements. What would be the solution?What we can do is to use PIM, and assign John as eligible for VM Contribute role. As per this solution John will not have permanent access to the resource. Whenever he needs the access, John would navigate to PIM console and requests for the desired access. He might be asked to provide a strong authentication (MFA) and approval might also be required. After the granted time window is elapsed his elevated privilege will be revoked.
Existing privileges
Currently John has read permission to the subscription. When he navigate to create a VM he will get following error message
Steps to gain Just in Time (JIT) privileges to perform desired actions
Step 1 : Administrator would log into PIM and click on Azure Resources
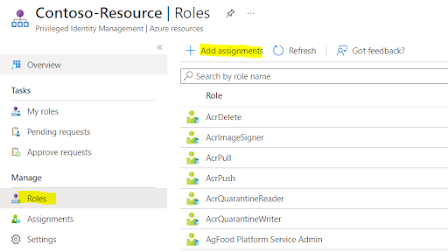
Step 2 : Click on Roles and click on add assignments
Step 3 : Select the role and select the user
Let's login to the PIM as John.
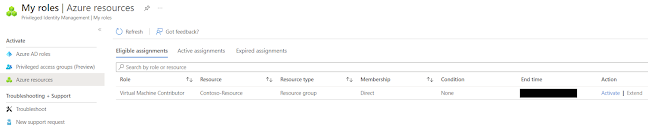
Step 1 : Navigate to My roles and Azure resources
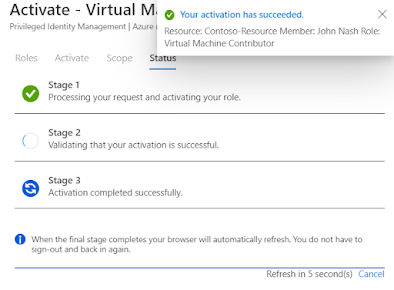
Step 2 : John will activate the privilege for 1 hour
Step 3 : Navigate to Active assignments in Azure resources blade in PIM
Now John should have access to VM resources, Let's see whether if he can create a VM.
Great!! Now we don't get the previous error. John's access will be revoked automatically after the expiry date or he can manually deactivate the elevated access.







No comments:
Post a Comment