There are bots and botnets on the internet constantly attempting to exploit vulnerabilities in applications for their advantage. Since Azure public IP ranges are readily available, the risk of such attacks is ever-present. IP ranges are available for various reasons and it is our responsibility to safeguard our assets.
In this article I will demonstrate how to identify such attempts to gain unauthorized access to our precious applications using Azure Monitor - Application Insights. Additionally, I'll illustrate how to safeguard our resources with Azure Front Door - Web Application Firewall (WAF).
Let's explore the process of detecting malicious attempts from bots.
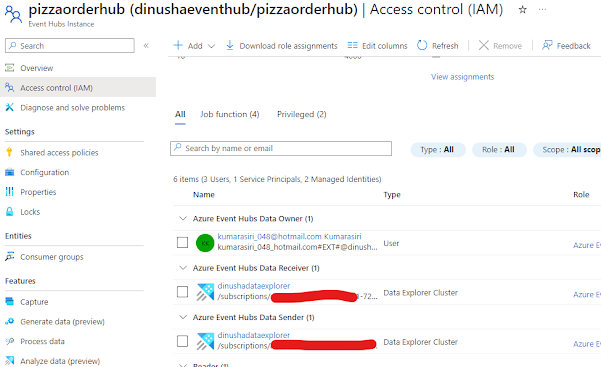
Navigate to Application Insights and go to the Failures tab. You will notice a substantial number of errors in the 400 category, particularly 404 errors as per the image below.
Let's identify the origin of those requests. There are several methods to achieve this. But I prefer the following approach. Navigate to Usage > Events > View More Insights.
Based on the origins of the requests, I can confirm that they are not acceptable.
Now that we have identified a risk, the next step is to safeguard our applications. If you have configured Azure WAF, the process is straightforward.
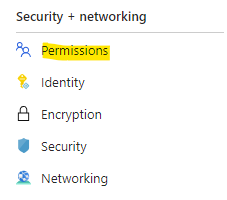
Let's navigate to Web Application Firewall (WAF).
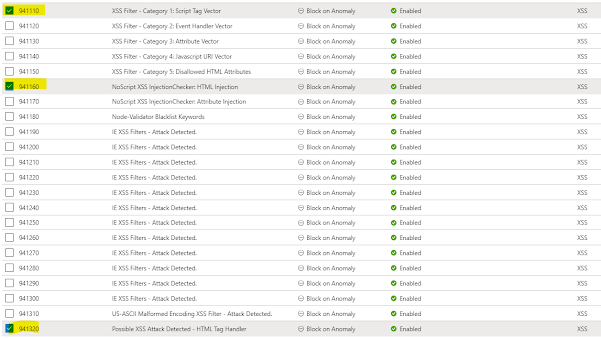
I have enabled only the Microsoft_DefaultRuleSet_2.1 as the set of rules in our WAF to filter requests. Unfortunately, it doesn't include any rules to filter requests from bots.
Fortunately, we can address this by adding an additional ruleset to my default rules. To add an additional ruleset, click on Managed Rules, and then click on the Assign button. In the Additional rule set option, select Microsoft_BotManagedRuleSet_1.0, as shown below.
Once it is applied, it will add another set of rules to handle bots
That concludes the necessary steps. Our application is now in good hands.