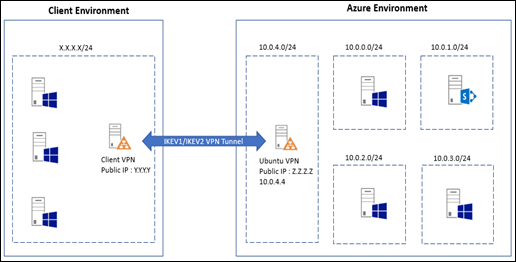
Microsoft Azure is a great place to host our IaaS workloads. We can create a complete setup using Azure IaaS features including but not limited to Virtual Machines, Virtual Networks, Gateways, etc..
It’s often a requirement to connect external networks to our Azure virtual network. Azure itself provides a great feature called Virtual Network Gateway which can be utilized to build Site-to-Site VPN connectivity with external network.
However, Azure Virtual Network Gateways still have some compatibility issues and other limitations. Some issues are as below
- Some routes are still not supported.
- We can use either IKEV1 or IKEV2 for a subnet but not both (either policy based or route based. but not both).
We don’t know, by the time you read this article, those issues may have fixed.
In my Azure environment, I have a SharePoint 2013 farm. I need to allow users from the external network to use my SharePoint farm by creating a trust between two environment. In order to perform that task I need a reliable Site-to-Site connection.
In this article I’ll show a reliable mechanism to create Site-to-Site VPN using a Ubuntu Linux VM and StrongSwan.
Following are the steps to be done at Azure environment
Prerequisites
- Create Ubuntu 14.04 VM in Microsoft Azure environment
- Public IP is available
- IP can be forwarded
- UDP ports 500 and 4500 is open
Steps
- Create Ubuntu VM and connect to it using SSH client like PuTTy
- Login as Root
sudo su
sudo apt-get update
- Install OpenSSH server
sudo apt-get install openssh-server
- Enable IP forwarding
echo "1" | sudo tee /proc/sys/net/ipv4/ip_forward
- Navigate to /etc/iptables.rules and add following section
*nat
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
-A PREROUTING -s 10.0.0.0/16 -j ACCEPT
-A POSTROUTING -d 10.0.0.0/16 -j ACCEPT
-A POSTROUTING -o eth0 -j MASQUERADE
COMMIT
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
COMMIT
- Install StrongSwan and Update
sudo apt-get install strongswan
sudo apt-get upgrade strongswan
- Navigate to /etc/ipsec.secrets and add following line. We will create the connection using Pre Shared Key (PSK) to create the VPN. We should create a matching entry in our client VPN device too.
Z.Z.Z.Z Y.Y.Y.Y : PSK "Password"
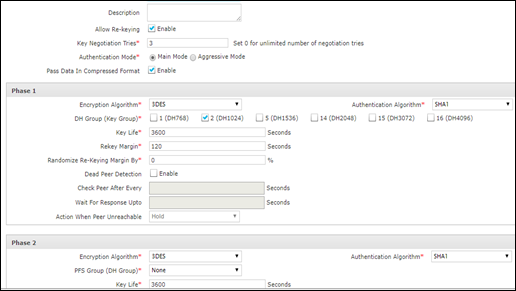
- Add configurations for each Subnet as below. In this sample I have shown how to build a IKEV1 connection.
conn Client1
authby=secret
type=tunnel
leftsendcert=never
leftid=Z.Z.Z.Z
left=10.0.4.4
leftfirewall=yes
leftsubnet=10.0.4.0/24
rightid=Y.Y.Y.Y
right=Y.Y.Y.Y
rightsubnet=X.X.X.X/24
keyexchange=ikev1
rekeymargin=120s
ikelifetime=3600s
keylife=3600s
ike=3des-sha1-modp1024!
esp=3des-sha1!
compress=no
keyingtries=3
reauth=no
rekey=yes
modeconfig=push
auto=routeBuilding IKEV2 connection is also similar.
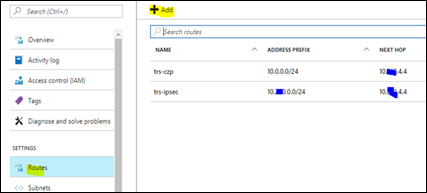
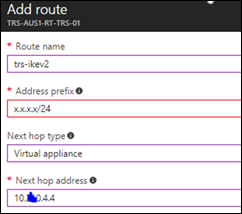
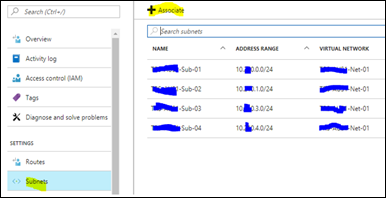
- Create a user defined route in Azure
- Start the VPN
- ipsec update
- ipsec secrets
- ipsec restart
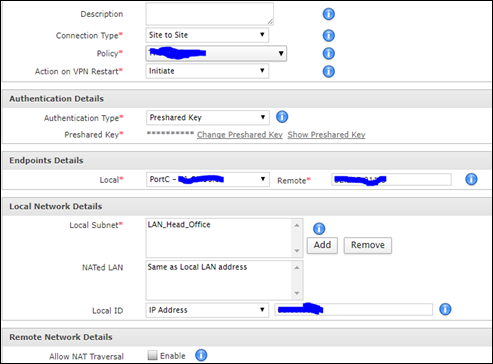
Following are the steps to be performed at client router
- Create VPN Policy
- Create VPN Connection
After completing above steps I’m able to establish a connection between my Azure environment and client network.
By using StrongSwan I can create multiple IKEV1 and IKEV2 connections to my Azure network seamlessly