You can have your applications hosted in Azure. How can you ensure that they are protected from various attacks?
We are safe if we can use an intelligent Firewall in front of our applications and ensure common attacks are addressed with the guidance of well recognized body, Isn't it.
We can use Azure Front Door and Open Web Application Security Project (OWASP) rules to achieve the above.
Let me explain how to do it.
We can implement a custom WAF policy and apply it to frontends in Azure Front Door.
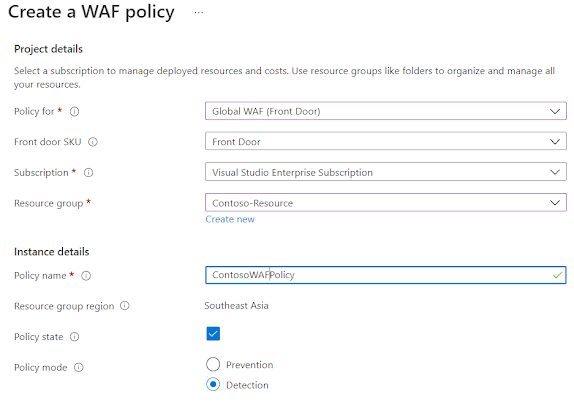
Step 1: Create a WAF policy
Step 2: Navigate to Manage rules section. OWASP rules are enabled by default. You can disable certain rules if you don't need them
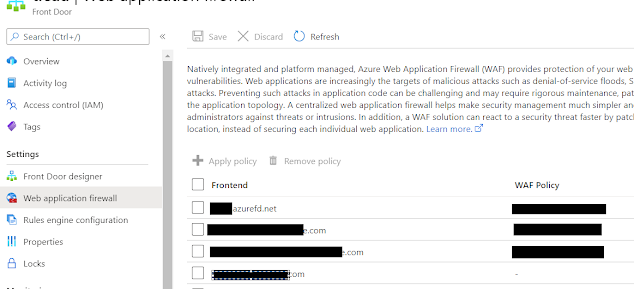
Step 3: You can apply the policy to Frontends in Azure Front Door easily by navigating to Azure Front Door instance
That's it. For any attacks the firewall will provide 403 response now.